Cloud migration shifted into overdrive during 2021 and the pace is unlikely to slacken over the next 12 months. By 2024, most enterprises will spend 80% of their IT hosting on the cloud, McKinsey predicted. The consultancy firm surveyed CIOs and business leaders and found that two-thirds (65%) said their organisation had increased its cloud budget as a result of the pandemic. It also said cloud will “unlock” one trillion dollars of business value in the coming years.
 Yet in the rush to move data, workflows and resources to the cloud, security is sometimes an afterthought – which is not necessarily surprising. Hard-pressed IT teams have to focus on making sure the cloud is operational and working at peak capacity, which is a demanding and time-consuming task. It is little wonder that security is neglected in the scramble to get the cloud up and running.
Yet in the rush to move data, workflows and resources to the cloud, security is sometimes an afterthought – which is not necessarily surprising. Hard-pressed IT teams have to focus on making sure the cloud is operational and working at peak capacity, which is a demanding and time-consuming task. It is little wonder that security is neglected in the scramble to get the cloud up and running.
At mid-sized companies, the threat is even more acute because enterprise-grade security has not been accessible – until now. To help you understand the threats and their solutions, we have compiled a rundown of cloud application security trends for 2021, as well as some predictions for 2022.
Cloud Assets Were a Top Target
In 2021, more data breaches involved cloud assets than on-prem assets, Verizon reported in its annual Data Breach Investigations Report. There was a decline in the number of laptops, desktops and other user devices being compromised as criminals and insiders focused their attention on the cloud.
“This makes sense when we consider that breaches are moving toward Social and Web application vectors, such as gathering credentials and using them against cloud-based email systems,” Verizon wrote.
A separate survey conducted by 451 Research found that 40% of organizations suffered a cloud-based data breach in the past 12 months.
In this era of remote and cloud-based workforces, businesses can’t afford for cloud security to be an afterthought.
Cloud Made Breaches More Expensive
The 2021 IBM Cost of a Data Breach Report found that companies with “higher levels of cloud migration” suffered a higher cost during a breach. When an organisation that has lagged behind on cloud adoption was hit by a breach, it faced an average cost of $3.46 million, whilst companies with more advanced cloud adoption programmes had to pay an average of $5.12 million.
“When the COVID-19 pandemic pushed more companies and industries into remote working, the result was an uptick in cloud migrations; this was accompanied by more costly breaches,” IBM wrote.
The risk posed by cloud depends on what stage a company has reached in its migration. Organisations at the beginning of their cloud journey reported increases in the likelihood of a breach, the median time to identify a breach, and the median time to contain a breach.
“For responding organizations early in their cloud migration, public cloud and hybrid cloud environments seem to have been challenging to secure and manage,” IBM added. “These challenges can result in higher front-end costs, as users employ more tools and software for the sake of securing cloud environments they don’t understand.”
Cross-Channel Attacks
Once upon a time, phishing was neatly contained in the inbox. Which meant that a good email security system could protect an entire organisation.
Those days are gone. Today, we are witnessing a huge rise in the number and ferocity of cross-channel, or multi-channel, attacks. These start in the inbox with a fraudulent email but draw victims out into dangerous cloud apps or malicious websites.
One analysis identified a 270% increase in social engineering threats in 2021, illustrating the scale of the threat.
Multi-channel attacks highlight the flaws of a security posture that relies on point products because it is no use having great email security if you don’t have cloud security. The solution is a platform like Censornet which defends organisations against threats in the inbox as well as in the cloud and on the web.
Predictions
Autonomous Security
It should not come as a surprise that the cybersecurity sector is facing a skills shortage, with more than three million positions unfilled across the world.
Automation will continue to be hailed as a bandaid for this problem in the coming year. Which is a reasonable position to take, because there is no doubt that automating routine tasks can save security staff from tedious manual work, alleviate alert fatigue and enhance the work of time-pressed humans.
But automation is just a waypoint on a much longer journey to autonomy. In the coming year, we will see autonomy continue to supplant automation. Working like an immune system, autonomous security systems are capable of responding to unknown threats more effectively than “cruise control” automated systems.
To find out what autonomy means for the security of your business, make sure you read about the Censornet Autonomous Security Engine.
Organisations Step Up to the Platform
Large companies enjoy the protection of enterprise-grade security which has, historically, not been available to the mid-market or SMEs. This is changing with the rise of platforms that incorporate several services into one security system. Censornet’s Platform, for example, incorporates MFA with web, email and cloud security.
Platforms are a force multiplier that offer mid-size businesses access to levels of security that would not be possible with point products. The analyst house Gartner said that organisations are “leaning into optimisation and consolidation” and predicted: “By 2024, 30% of enterprises will adopt cloud-delivered secure web gateway (SWG), cloud access security brokers (CASB), zero-trust network access (ZTNA) and firewall as a service (FWaaS) capabilities from the same vendor.”
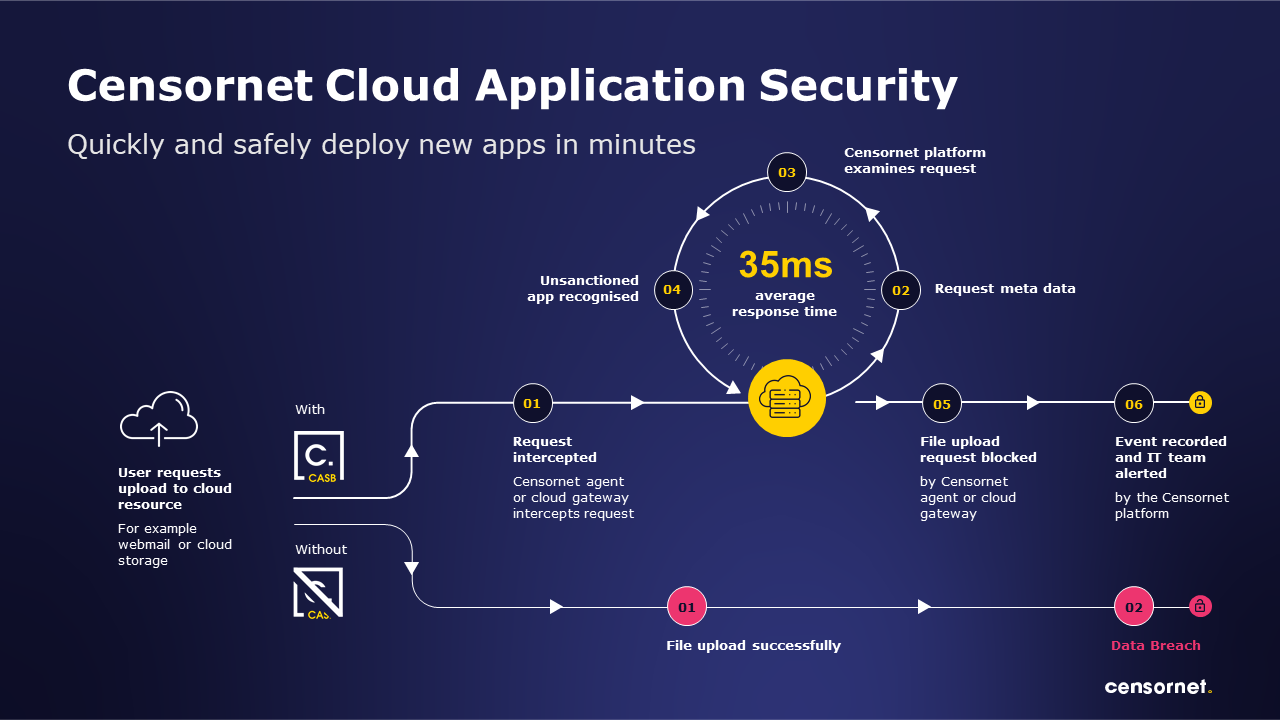
Cloud Application Security (CASB) Will Become Non-Optional
Censornet has often said that Cloud Application Security (CASB) is no longer a “nice to have”, but a must-have. This statement will become ever clearer throughout 2022.
Cloud Application Security allows organisations to secure, monitor and manage user interaction with cloud applications, defending a modern remote workforce and offering protection against a range of risks including insider threats.
The number of incidents involving insiders grew by 47% between 2018 and 2020. There is good reason to believe this growth will continue. A CASB can defend against this threat, whilst also protecting against cloud-borne malware and forming part of a unified defence against multi-channel attacks.
Work is no longer a place, but an activity. Discover what that means for cybersecurity