Seamless discovery, analysis and management of user interactions with cloud applications. Achieve complete visibility and control with a full-featured CASB solution and protect your modern mobile workforce.
Discover every cloud app used on your network and control their actions with our 1,500+ app catalogue.
Inline and API ‘multimode’ CASB solution maximises visibility and protection and eliminates blind spots.
Revolutionary DirectProtectTM architecture to eliminate proxy and geolocation difficulties.
Salesforce
Microsoft OneDrive
Outlook
ILovePDF
ChatGPT
Claude
Copilot
Amazon

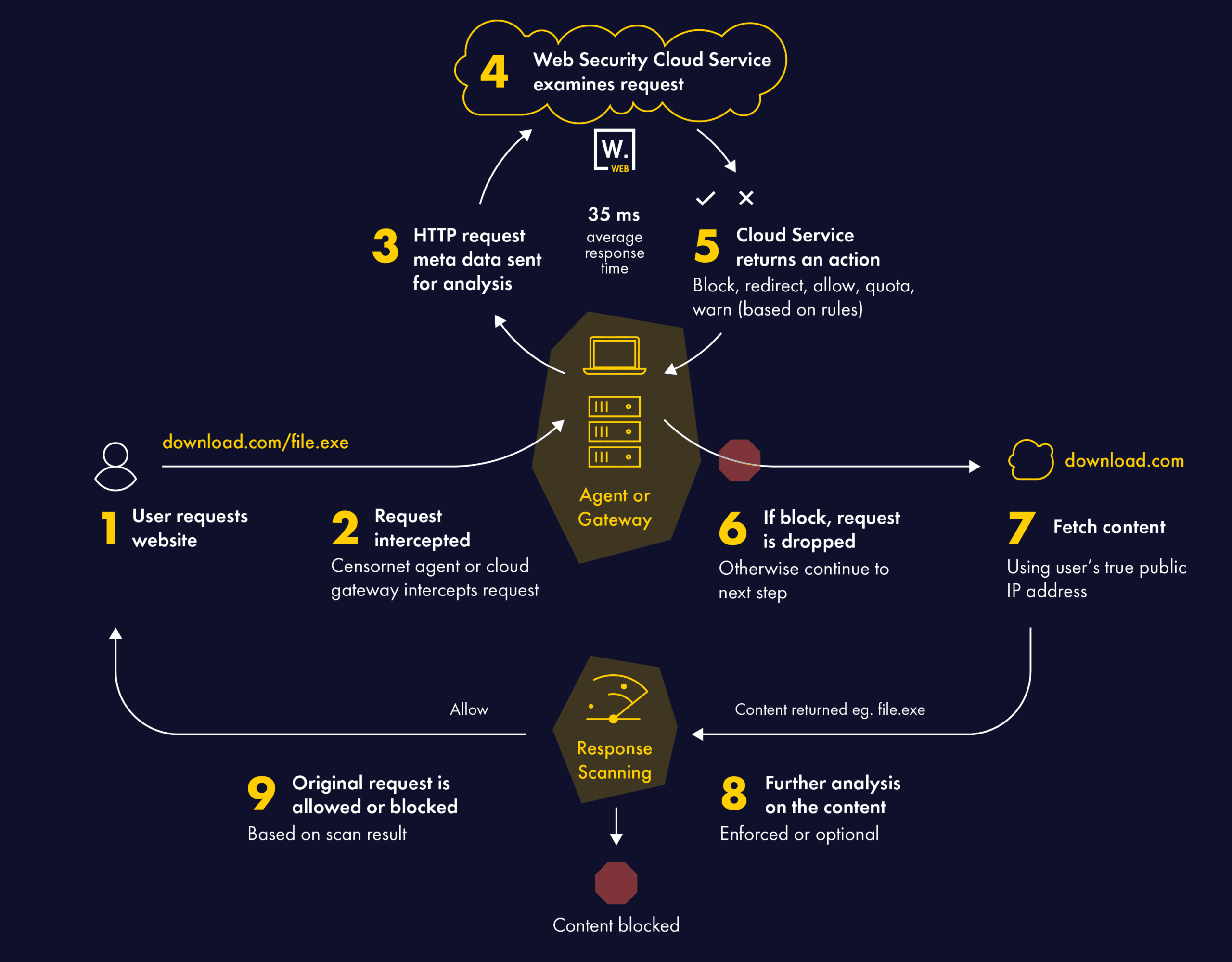
Protect your organisation from web-borne malware, offensive or inappropriate content and manage time spent on websites that impact productivity with Censornet Web Security. Powered by a unique architecture that ensures lightning fast response times for all users no matter where they are in the world.
Discover every cloud app used on your network and control their actions with our 1,500+ app catalogue.
Discover every cloud app used on your network and control their actions with our 1,500+ app catalogue.
Discover every cloud app used on your network and control their actions with our 1,500+ app catalogue.

Ultra-modern multi-layered email security solutions for your entire organisation from known, unknown and emerging email security threats. Stop large-scale phishing, targeted attacks, impersonation fraud and malware in their tracks with a comprehensive, cloud email security solution.
Using multiple technologies, Censornet ensures enterprise class threat detection rates with very high accuracy – over and above what single engine solutions can provide.
Email Security combined with a full cloud based mail routing engine. Easily support multiple email service providers within a single domain and migrate between providers with ease.
Native integration with enterprise-grade DLP for ultimate email protection and data security.
Reduce email data risks, optimise storage costs, and improve productivity.
Analysis has shown that as much as 60% of business data is stored in email – and much of it exclusively (Source: IDC).
The Compliant Email Archive from Censornet captures and stores every message sent or received in a separate, secure, tamper-proof database in the cloud. Archived messages are de-duplicated, compressed, indexed and encrypted.
An intuitive search interface – accessible from any device – allows IT, HR, and end users themselves, to quickly find emails using multiple search criteria. Privileged users can rapidly search all mailboxes, or selected mailboxes, to respond to internal or regulatory requests.
Censornet SecureMail is an add-on to Email Security and provides a simple, yet effective, solution for user-based encryption of specific messages.
Adding a customisable keyword to the start of the email message subject sends a message containing a secure link to the recipients that log in to a secure website to view the contents of the message.
SecureMail complements the policy-based encryption capabilities integrated within Email Security, with the ability to enforce the use of TLS for specified domains, as well as to use Opportunistic TLS for all messages – falling back to non-encrypted connections only if the receiving email server does not support TLS.
Add an extra layer of enhanced protection to Email Security.
The optional Advanced Email Sandbox protects against today’s evasive zero-day threats by providing a highly scalable and powerful environment to run in-depth, sophisticated analysis of unknown or suspicious programs and files.
The Advanced Email Sandbox service adds a powerful layer of protection to Email Security, alongside multiple tier-1 signature and behaviour-based antivirus (AV) engines. The Sandbox service analyses suspicious files in depth, detonates payloads in a contained virtual environment, scrutinises their behaviour, and identifies malicious intent.
Sandbox technology provides advanced threat protection and zero-day exploit detection by:
Censornet’s Advanced Email Sandbox is a cost-effective sandbox solution for protection that goes above and beyond that provided by standard antivirus engines.
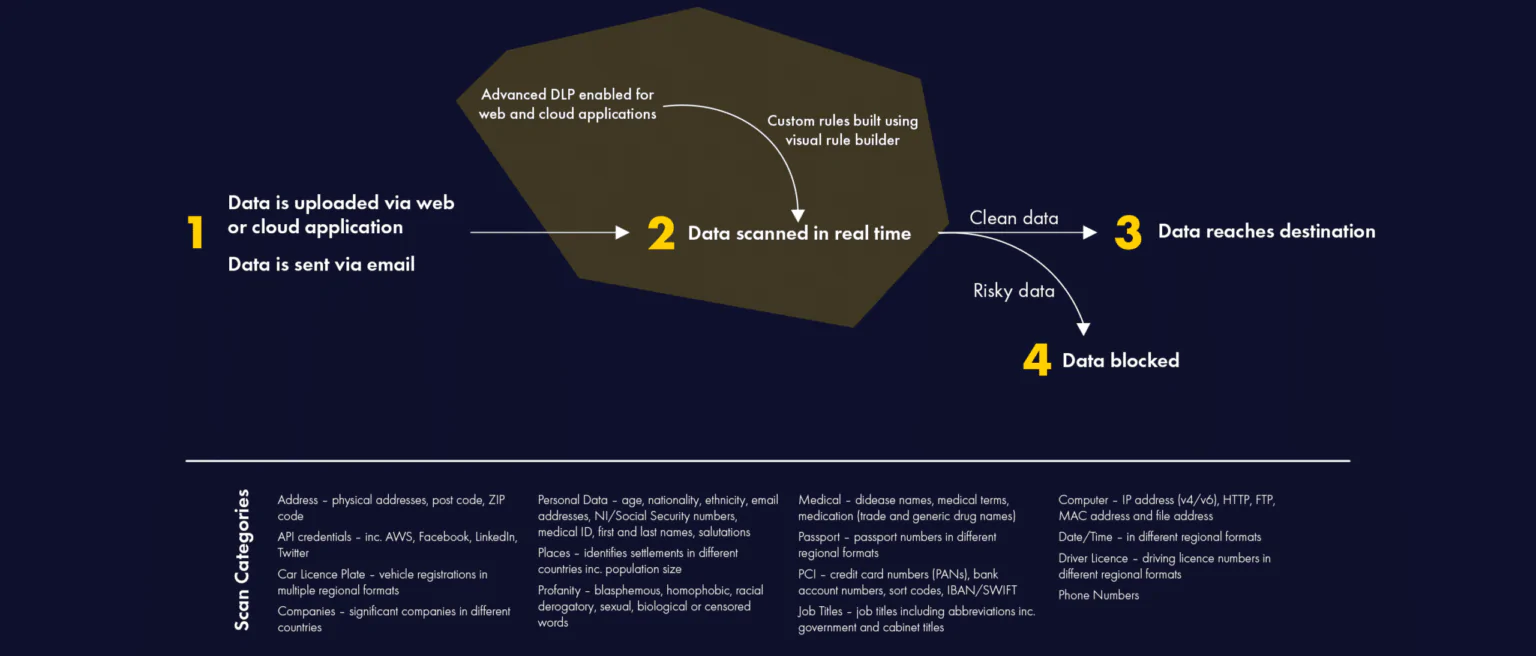
Enabling real-time discovery and blocking of confidential or sensitive data in flight with the ultimate data protection solution for businesses. Built with advanced detection and prevention capabilities, our enterprise-grade DLP protects your sensitive information from unauthorised access, accidental disclosure, and malicious attacks.
Reduce risk and ensure compliance with legislation and regulations, including GDPR, with support for personal data (Personally Identifiable Information) in 58+ countries and 38+ languages.
Fully integrated with Censornet’s autonomous integrated cloud security platform and with a single policy engine, you get immediate data protection out-of-the-box with intelligent, behaviour-based templates.
With real-time discovery and blocking of confidential or sensitive data in flight, you can be confident your data is safe across email, web and cloud applications.
Exact DLP content analysis and actions can be implemented on top of existing rules to provide immediate data centric intelligence – and prevent data loss in real-time.
Introducing integrated MFA and IDaaS. Secure access to a wide range of systems, services and applications using an adaptive, cloud-based multi-factor authentication solution or single sign-on (SSO) to automatically authenticate users with the richest possible contextual information. Protect user accounts with more than just a password and reduce the impact of password reuse when the next large scale data breach happens.
100% cloud-based back end, simplifies implementation and accelerates time to value for organisations of all sizes.
Adaptive authentication delivers a friction-less user experience – intelligently challenging users only when risk is high.
Out-of-the-box support for a wide range of systems, services and applications including all major VPN vendors and cloud applications.
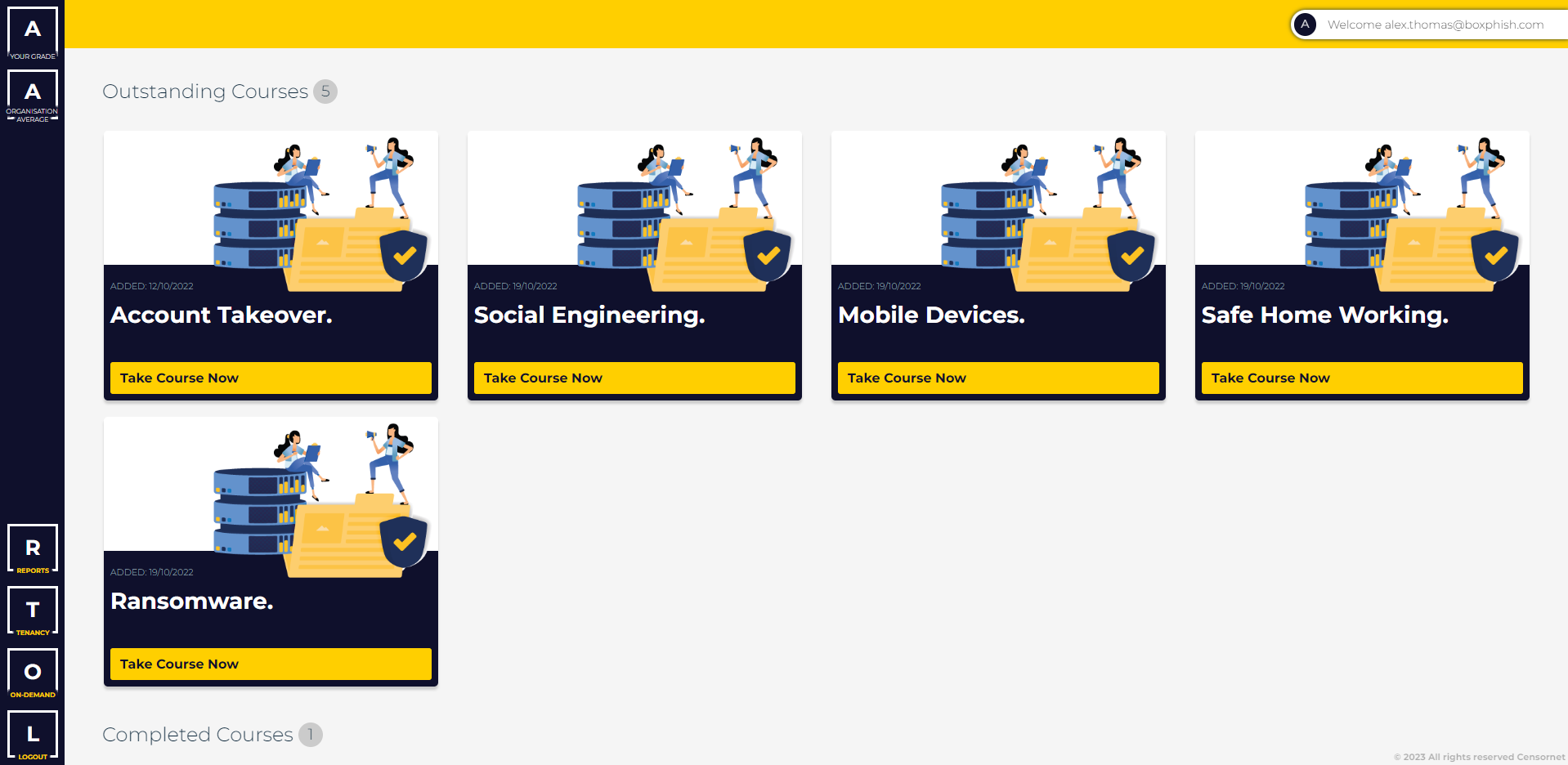
Defend your organisation against cybercriminals and strengthen your ‘human firewall’ with our engaging, automated training. Run realistic phishing simulations, grow your staff’s cyber defence skills, and track effectiveness with detailed reports and dashboards.
Automated platform allows you to roll out training to your whole organisation at speed and within budget.
Deliver immersive phishing simulations to train staff through practical action, and reinforce learning with engaging online content.
Detailed, data-driven dashboard lets you track your human cyber risk and identify how to maximise your defence.
If you wish to chat to someone about our products or services please contact our UK office on the number below:
0845 230 9590
Adding {{itemName}} to cart
Added {{itemName}} to cart