Last month, ZDNet reported that Teensafe – which markets itself as a secure app to let parents monitor their children’s phone activity – had left two of its Amazon cloud servers public. This meant that data such as plaintext passwords, parent email addresses, and device names were exposed for more than 10,000 children and viewable by anyone, without even requiring a password.
Time and time again we see organizations of all sizes making vast volumes of highly sensitive data public through what seems to be little more than a configuration error. Teensafe is just the latest company in a series that has left data exposed through AWS, with recent cases including FedEx, Verizon and Uber.
In fact, last year 69 percent of exposed records came at the hands of unintentional exposure due to accidental leaking online and misconfigured services and portals. [1] The extreme sensitivity of TeenSafe’s data, and the fact that the entire company is built around the promise of protecting children, makes this case all the more shocking. The volume of the data exposed, and nature of this data makes this a significant breach, and there are a number of lessons that companies should be taking away.
Firstly, organizations should take note that this vulnerability – like many others – wasn’t created by a hacker, it was created by staff. While it is right to prepare your organization against external threats, companies shouldn’t forget their own employees are as likely – or even more likely – to put company data at risk. After all, why would a hacker go to the effort of breaching a company’s defences if they could easily find all the data they need online? The bottom line is, organizations need to get a handle on the human element, which means training, rigorous procedures, and technology that helps IT teams gain insight into the company’s employees’ actions.
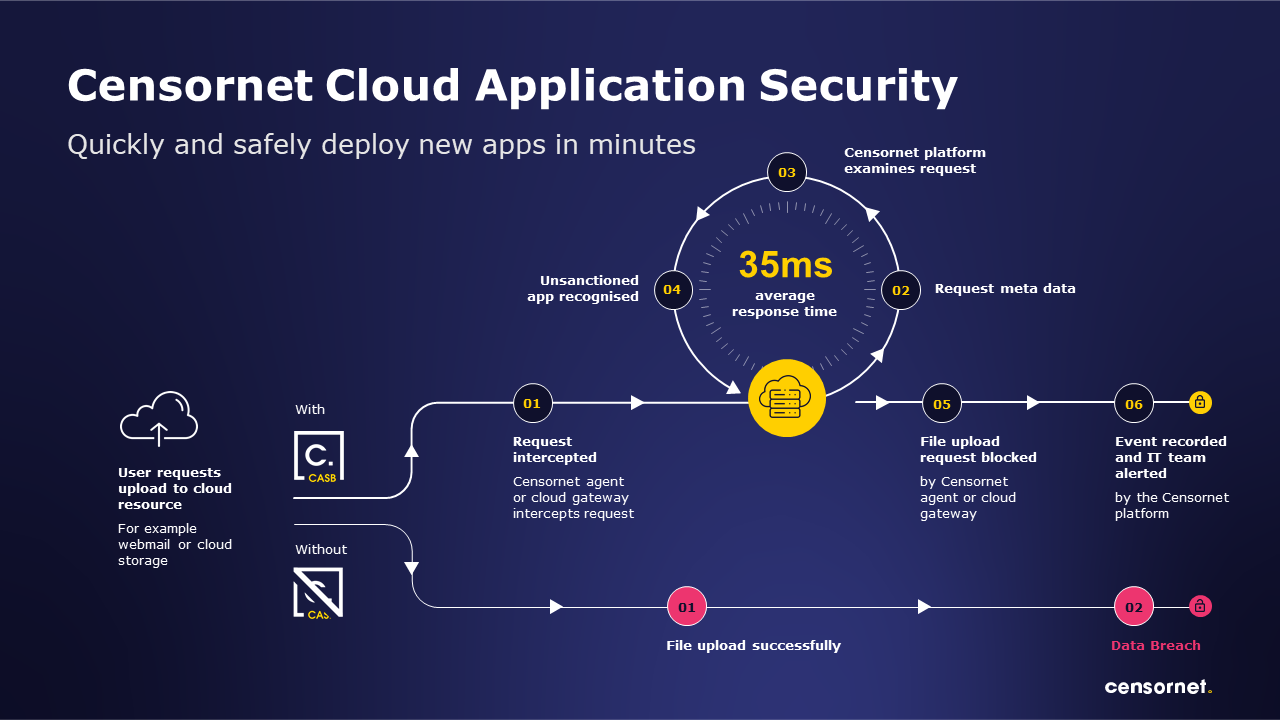
Secondly, companies absolutely have to get a better visibility and control of their cloud servers and solutions. The cloud changed everything for security, taking data off company premises and placing it in the trust of third parties. However, these environments can be secured with the right procedures and the right tools.
What the Teensafe data breach, and preceding AWS data leaks, smack of is companies still not having got to grips with cloud security. In this realm, especially with the GDPR, visibility is key. Organisations need to know where there data is and who can access it as a bare minimum. And this goes for the cloud solutions running within your organisation, as well as your cloud storage.