How many specialised security products does your organisation currently use?
Statistically, the number is likely to be high. The average small-medium organisation uses 24 point-products to protect themselves.
In adapting to a cloud-first world, organisations have inadvertently created a huge attack surface by deploying multiple security products. Hackers can easily exploit the gaps between all of those siloed point products. This isn’t the only thing causing a headache for IT security teams. Mid-market organisations are facing a perfect storm: an unmanageable number of products, an overload of cyber alerts, and a difficulty attracting and then retaining team members, all while budgets are being stretched thinner and thinner.
In this blog series, we will investigate how mid-market organisations can navigate these challenges. We’ll drill down into how security vendor consolidation can provide a solution and the questions security leaders should ask themselves as they start this journey. Today, we are going to take a look at the problems consolidation can solve and why it’s particularly relevant for the growing mid-market.
Too many products, too little sleep
Too many mid-market businesses are managing disparate point products and incompatible dashboards, whilst struggling to integrate new systems with existing defences. Overall, 27% of mid-market firms rely on over 31 security solutions and 7% deploy more than 501. The substantial operations overhead that comes with managing this number of products is cumbersome and unnecessary. It also means increased training requirements, poor visibility of the whole security ecosystem, and increased manpower to respond to individual alerts that pour in from each product.
According to our UK Mid-Market On Code Red report, the round-the-clock threat of attack and the stress it causes means that the average amount of sleep someone responsible for cybersecurity gets is 5.7 hours, significantly less than the seven hours or more recommended by the NHS2.
 With stretched security personnel facing a barrage of security alerts, nearly half (47%) admit to feeling overwhelmed when faced with too many cyber security alerts, while 31% are unable to cope following prolonged periods of work-related stress and burn-out. It’s no wonder then that our research shows nearly half (46%) of organisations in the mid-market want to see security vendors open up traditionally closed point products to enable an automated response to cyberattacks.
With stretched security personnel facing a barrage of security alerts, nearly half (47%) admit to feeling overwhelmed when faced with too many cyber security alerts, while 31% are unable to cope following prolonged periods of work-related stress and burn-out. It’s no wonder then that our research shows nearly half (46%) of organisations in the mid-market want to see security vendors open up traditionally closed point products to enable an automated response to cyberattacks.
Consolidation a priority already
Across all sized businesses, consolidation is accelerating. According to Gartner, 75% of organisations are pursuing a vendor consolidation strategy, up from 29% in 202024. It’s becoming clear that consolidation, when done correctly, is an effective strategy to help navigate the ever-evolving threat landscape, product overload and the uncertain economic climate. In fact, Gartner states that already, 57% of organisations are now working with fewer than ten vendors for their security needs4.
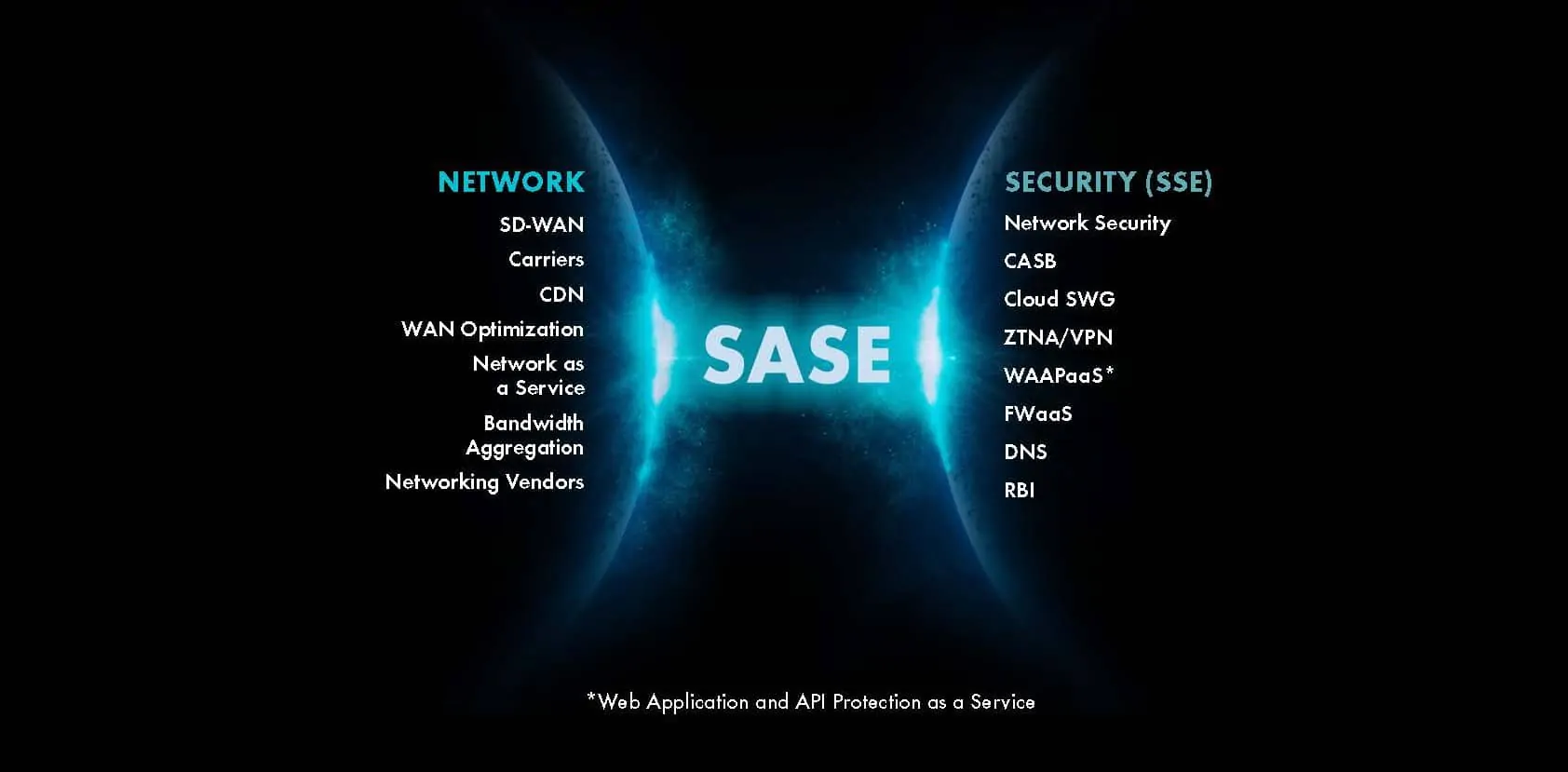
What is security vendor consolidation for the mid-market?
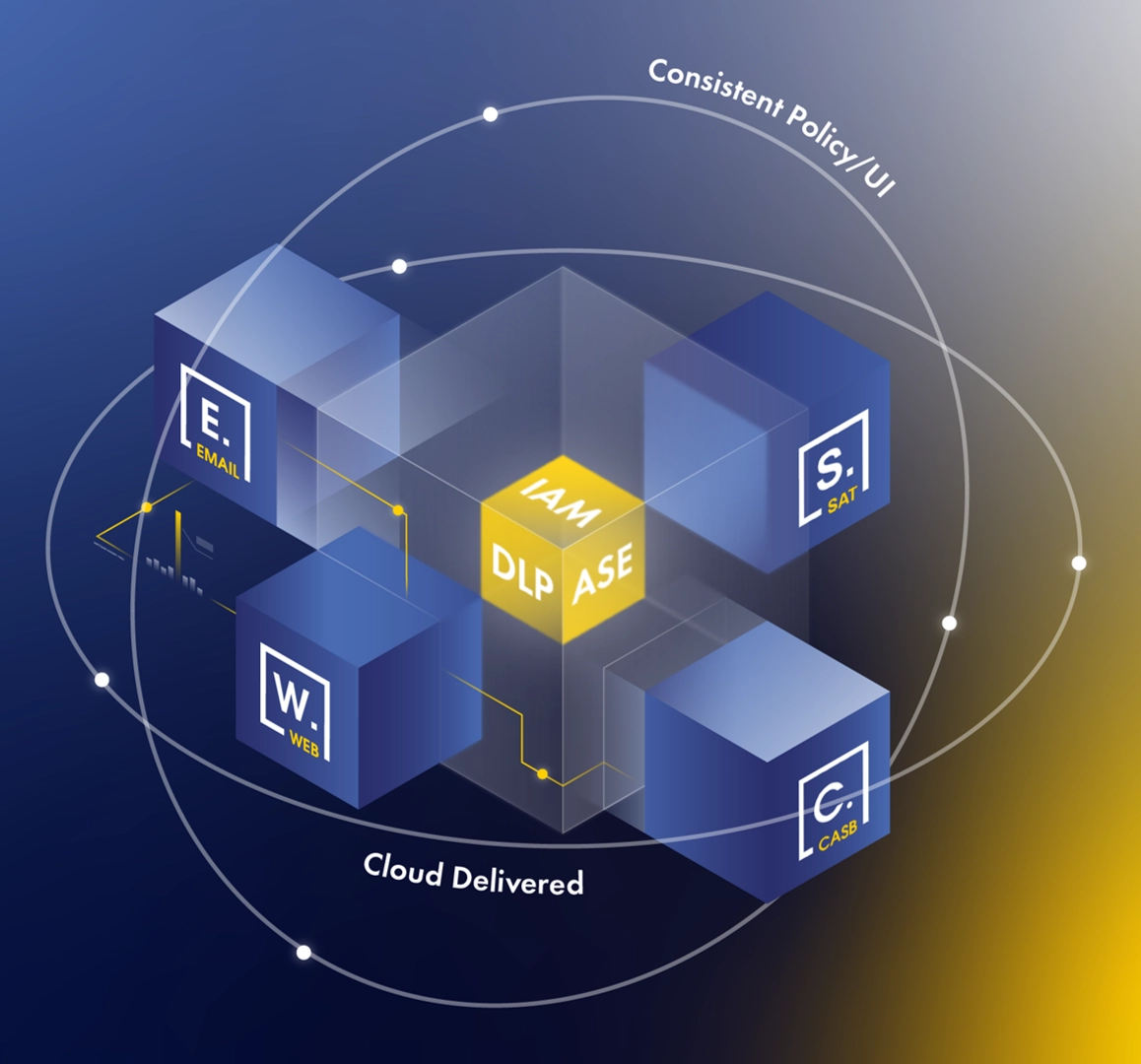
It means taking a more coordinated approach. Email, web, identity, and cloud application security systems work in tandem, identifying and tracking attacks before they proliferate across an organisation. By implementing a consolidated approach, security teams can gain a holistic view of their security systems and achieve tighter integration between previously disconnected security products, ultimately improving their threat detection and response efficiency.
And perhaps most importantly, consolidation allows for a truly digital business. A consolidated approach gives users the freedom to access the applications and data they need regardless of device or location, whilst providing visibility for IT and adequate protection. It also comes with the added benefit of reducing costs and protecting the wellbeing of security teams. In today’s current operating climate, this is more important than ever.
Over the next few weeks, we’ll be taking a deeper look at all things consolidation: the questions IT teams should ask before beginning on the journey, the positive impact it can have on reputational protection and the difference between consolidation and integration.
Can’t wait for the next blog? You can download the Gartner® Infographic behind the series now.
4Gartner, Infographic: Top Trends in Cybersecurity 2022 — Vendor Consolidation, John Watts, Dionisio Zumerle, 19 August 2022. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.