
After software ate the world, the cloud cannibalised your perimeter security
The dissolving boundaries of the last twenty years have left many uncertain
In 2011, Marc Andreesson famously predicted that software would eat the world. First, it came for the physical things. Remember the book shop Borders? It was rapidly digested by a small online book retailer, called Amazon. It didn’t stop at books either, gobbling up media, transport, retail and just about any other sector it could swallow.
This has had a huge impact on the enterprise. Companies have come to rely on a wholly digital workplace. Software tools are now as much a part of business infrastructure as water, power and human resources.
The world has recently hit a second tipping point in this transformation – shifting the enabling technology from inside, to outside the network. Software and hardware now no longer reside inside an easily definable, controllable perimeter.
Mobile working killed any notion of protecting devices and connections, social media democratized company networks and all the applications now reside in a gigantic server farm. Sadly, this means so do most of your communications, databases, spreadsheets, schematics and other IP.
This has changed the way these assets NEED to be protected. The question is, has it changed the way your assets ARE being protected? To answer this, it’s important to track back through history to understand a few key shifts: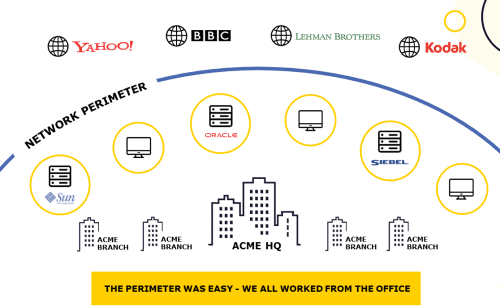
1999
A seminal year for business software disruption. Firstly, BlackBerry was launched. If anything caused a flex in the perimeter, it was the mind-set shift when email was no-longer desk bound. The first USB drives were also developed, and data became an easily extractable commodity for the first time. Finally, Salesforce was launched – opening the first tiny cracks in the dam that now sees applications flowing out to the cloud. The majority of traffic was still internal however and there probably wasn’t even a WAN.
2009
Ten years later, things had changed a lot.
Steve Jobs had taken the helm at Apple, bringing a vision for a device that was essentially an open software platform. This has probably done more to melt the perimeter than any other device, bringing unfiltered data and external connections onto the network.
Bring your own device (BYOD) and remote working became a security risk. The SaaS business model was also starting to take root, with Microsoft 365 preparing for a beta launch late in 2010. Enterprise software was queuing at the door, ready to jump into the clouds.
2020
The ten years between 2010 and 2020 saw a rapid acceleration in perimeter security erosion.
The final quarter of 2017, for the first time, Microsoft saw more revenues from Microsoft 365 than from its physical software counterpart. In 2012, Amazon Web Services ceased being a separate division and became part of Amazon, where it now generates 12% of all profits through customers such as the US Navy, NASA and 80% of Germany’s DAX.
The vast majority of enterprise traffic data flows have now become external. It is safe to say, there is not much left inside the perimeter. Even Active Directory is being outsourced to Azure.
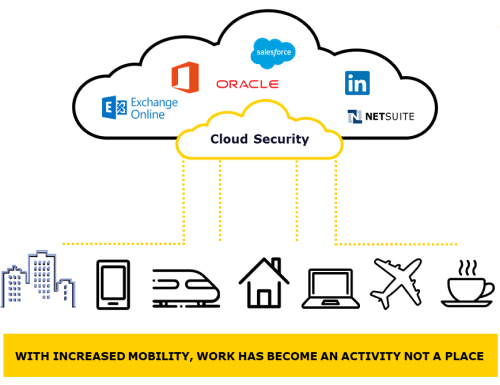
So what does this mean for security?
The simple answer is to embrace this seismic change. Employ a security platform built for the cloud, not retrofit a collection of technologies from a bygone era.
Point solutions still have a place but are nowhere near holistic enough. What is required is technology which can collect, analyse detect and act on the mass of traffic which now constitutes organisational data flows into the cloud. It must do this in context, understanding that malicious traffic from someone uploading financial data to Facebook, looks different from someone sharing weekend snaps. Without this understanding, cloud-based business is inhibited. Protective arms become strangling.
Modern cyber security must also understand the other facets that come with working in a cloud-native world. Availability, is crucial. Cloud-based businesses are 24 hours per day – so how can security ensure uptime, even when primary data methods fall over?
User experience is another vital element. We live in a world where seamless UX is not only desired, but expected, something which legacy security approaches are at odds with. Contemporary cyber security must understand this and take an enabling position, rather than that of stern security guard.
Compliance is also crucial. As the cloud forces an ever-growing raft of emerging data problems, regulation is growing, so having the ability to audit users in a granular way not only saves time and money, but also protects brand.
These rules and more form the basis of our countermeasures targeted at a world which is still undergoing undeniable change.
The perimeter is rapidly accelerating out of existence and in a world where the frontiers are being redefined, security technology must change. As Marc Andresson said, companies must seek to understand and hold on tight, otherwise there is a risk they may get consumed. The same goes for security in the modern age.
Find out more at our Defence365 hub.