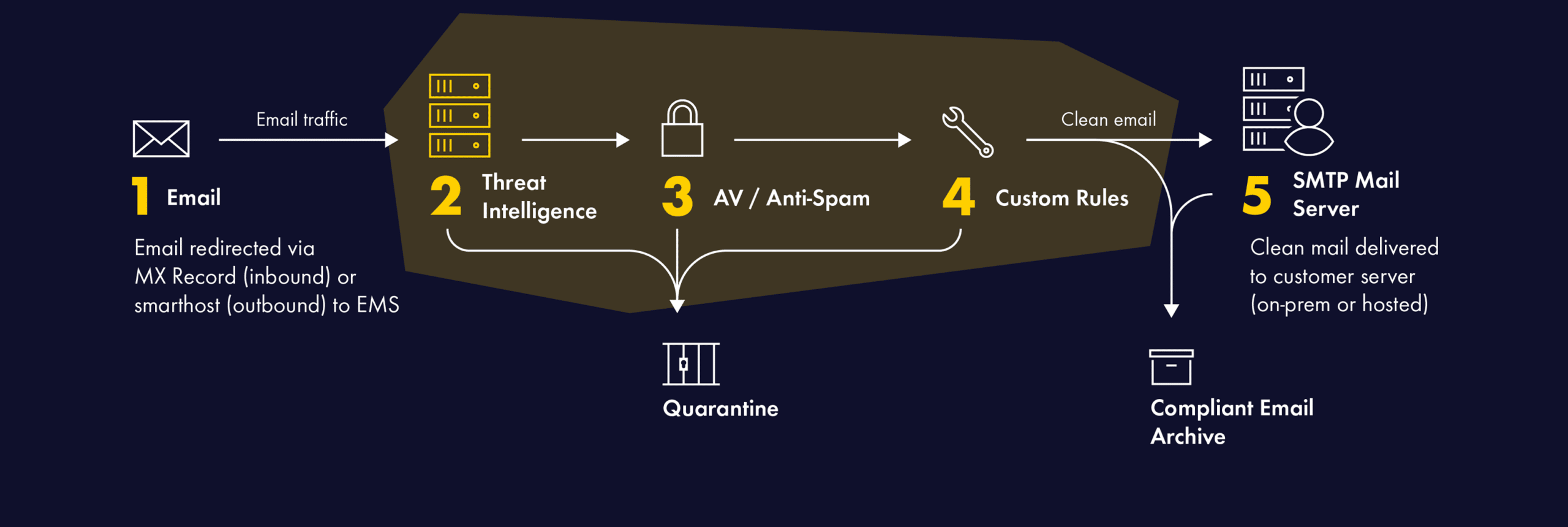
The end of life for security solution isn’t just an event; it’s a crossroads. With Forcepoint‘s recent announcement about the end of life for its email security, many are left navigating this crossroads, seeking clarity amidst the complexity. We explore the road ahead, and the next steps organisations can take.
Forcepoint‘s Journey: Understanding the Landscape
Whilst Forcepoint has long been a recognised name in the cybersecurity landscape, it hasn’t been without its challenges. From concerns about threat visibility, particularly in areas like phishing email protection, to feedback about the need for more responsive and knowledgeable technical support, users have highlighted several areas for improvement. Most notably have been the performance and integration challenges.
Given these considerations, the announcement of its end of life might be seen in a different light. Perhaps it’s an opportunity for organisations to explore solutions that better align with their evolving needs and the ever-changing cybersecurity environment.
Transitioning away from a familiar security solution can be daunting. It brings up challenges that aren’t just technical; they’re strategic, operational, and even emotional for some. Despite being end of life, the hesitancy to move can stem from various reasons, including migration challenges, apprehensions about new software features, or simply the comfort of the familiar.
How to Transition from Forcepoint Email Security
Choosing an alternative to Forcepoint email security is not just a matter choosing an active product: it’s a balance between the technical and the strategic. Before any significant decisions are made, it’s crucial to assess the impact on the organisation. What will the transition mean for daily operations, for long-term goals, for stakeholder expectations?
Effective planning, often encapsulated in a lifecycle management plan, is the cornerstone of a successful move. It not only reduces vulnerabilities, but minimises downtime risks and ensures compliance. But what’s a strategy without a clear understanding of the terrain? This is where a thorough network inventory comes into play. By leveraging device management software, organisations can capture essential information about their devices, painting a clear picture of their digital landscape.
Amongst all this, one thing remains constant: the need for robust cybersecurity. Even in the throes of transition, the shields must remain up. This means not only maintaining current security measures but also implementing additional ones to bolster defences in the long run.
This transition can be a strategic move that shapes the trajectory of an organisation’s security. Engaging stakeholders, from team members on the ground to the board in the boardroom, is crucial. A transparent dialogue can foster trust and ensure its smoother for all involved. It’s an opportunity to bolster defences, realign with the evolving digital landscape, and chart a course towards a more secure future.
Forcepoint Email Security Alternative
The end of life for Forcepoint‘s email security should not be seen not as a setback, but as an opportunity to embrace a new era of cyber protection. Analysis shows Censornet’s Email Security as a cost-effective alternative, offering a fusion of enterprise-grade cyber protection with the agility and responsiveness tailored for SMBs.
Censornet’s Email Security offers a multi-layered approach, with comprehensive protection from email threats such as large-scale phishing, targeted attacks, impersonation fraud, and malware. It’s a complete cloud email security solution that ensures threats, both known and emerging, are stopped in their tracks. This isn’t just about addressing the gaps; it’s about setting a new standard.
What truly sets Censornet apart is its commitment to innovation and its award-winning support. In a digital landscape where threats evolve continuously, Censornet’s deep machine learning capabilities ensure that not only are threats identified, but they’re also anticipated, allowing IT teams to focus on strategic imperatives rather than getting bogged down by minor alerts or false positives.
For organisations looking to transition from Forcepoint, Censornet doesn’t just offer an alternative; it offers a vision of what modern, integrated cybersecurity can and should be. It’s a vision where email, web, and cloud application security converge seamlessly with powerful identity management and data loss prevention, ensuring that organisations are not just protected but empowered.
Censornet
Forcepoint
Ease of use
Cost
£
££
For organisations looking to transition from Forcepoint, Censornet doesn’t just offer an alternative; it offers a vision of what modern, integrated cybersecurity can and should be. It’s a vision where email, web, and cloud application security converge seamlessly with powerful identity management and data loss prevention, ensuring that organisations are not just protected but empowered.