The current crisis has thrown a lot of long-standing business processes into confusion. For the security and IT function, the main issue is how to protect remote workers, which is apparent by the interest in our recent remote working security webinar Q&A.
With a surplus of information out there on this topic, some might find it hard to traverse the volume of advice and opinions. For this reason, we decided to provide a brief summary of accepted best practice from some of the standards bodies tasked with collecting and delivering neutral advice for secure remote working.
ISO27001
For high-level guidance, ISO27001 provides a good start-point. ISO standards are sometimes criticised for a lack of detail on specific technical controls, however for a team looking for solid grounding, they can be a good start point.
ISO’s risk-based approach is intended to be technology-neutral, providing frameworks for companies looking for advice rather than going into specifics. It does this by breaking security down into a set of proposed policies and encouraging the user to conduct risk assessments to reach a final objective.
Section 6.2 of ISO 27001 covers remote working, splitting it into two parts: mobile device policy and teleworking. Using this part of the standard, those responsible for security are walked through a process of understanding the following facets of their organisation and encouraged to develop policies around them to help protect remote workers:
-
Who can telework?
-
Which services should be made available to them?
-
What information is available remotely?
-
What access controls should be in place?
-
How to configure devices and cloud-hosted services?
National Institute of Standards and Technology (NIST)
For more specific detail, the US-based National Institute of Standards and Technology (NIST) is often looked up to. The organisation has been driving the development of cyber security standards for a number of years.
deals specifically with the securing of devices, teleworking and remote access policies. This publication leads by urging organisations to consider the following five ground rules when building a remote working security policy, taking some time to outline proposed solutions in the following report:
1. Plan telework-related security policies and controls based on the assumption that external environments contain hostile threats
2. Develop a telework security policy that defines telework, remote access, and BYOD requirements
3. Ensure that remote access servers are secured effectively and configured to enforce telework security policies
4. Secure organization-controlled telework client devices against common threats and maintain their security regularly
Whilst more specific in detail than ISO, the NIST standard is still a little outdated when it comes to outlining remote access architecture. It covers tunnelling (VPNs), portals and virtual desktops – but as it was written prior to the mainstream adoption of many modern cloud applications it only touches lightly on ‘direct application access’ – citing webmail.
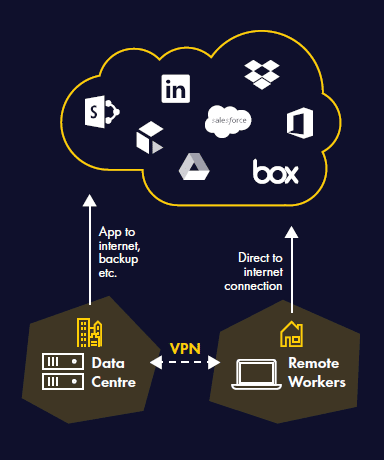
This is a little behind the ball in today’s SaaS-happy enterprise space. Conspicuous by its absence, for example, is the common practice of split tunnelling. This is where enterprise users have access to both a VPN connection to a data centre, but also direct-to-internet connection for services like Microsoft 365. Such practices are now simple to protect using solutions such as Censornet.
The other relevant NIST publication is NIST SP 800-53 Rev. 4,
which goes into greater detail about specific security and privacy controls to implement. It should be considered as guidance for organisations looking for a ‘consistent, comparable and repeatable’ approach for selecting and managing security controls.
In summary, amidst a threatening and unprecedented situation security teams scrambling to understand what ’good’ looks like, can turn to such standards bodies for initial outline guidance. They provide a trusted and independent grounding for policies, rather than the policies themselves.
However, be warned that such standards bodies are typically attached to slower moving organisations and there may be some gaps as they await updating. This is where more contemporary specific advice, such as provided by our on-demand webinar and ‘Secure Remote Working Tips’ eBook can help – find this advice and more on our Secure Remote Working page.






