Take a minute to think about how many SaaS applications your business relies on across the web and the cloud… Then think about the cyber risk each one introduces.
According to Gartner, the average company uses 335 SaaS applications! Besides ‘standard’ workplace systems like Slack, Salesforce, and Google Drive, it’s now the norm for countless other functions, like accountancy, planning, file sharing, etc., to each have their own dedicated software.
But despite the growing number of apps, the goal remains largely the same: improve business productivity. And it works; a Google study found that “SMEs using the cloud grow 26% faster and are 21% more profitable than their peers”. And market intelligence firm IDC found that “almost every SME that uses cloud services saves money, with most lowering costs between 10% and 20%”.
So, what’s the catch with productivity apps?
In reality, each of those ‘solutions’, while aiming to boost productivity (and all the benefits that come with it), could introduce cyber risk that achieves the exact opposite effect. Potentially, each one could be the cyber straw that broke the camel’s back – and the vulnerabilities could have dire consequences…
Imagine facing situations like these:
Confidential data leaks out of your organisation. That’s what happened to genetic testing company 23andMe. Hackers managed to access DNA data for almost seven million of its users, with at least two-dozen people subsequently filing lawsuits against it for negligence. The damage to the company’s reputation saw its valuation drop 91% within a year of it admitting to the breach.
Malware seeps into your organisation. Credit reporting agency Equifax was famously subject to a malware attack in 2017. It enabled hackers to harvest personally identifiable information including birth dates, addresses, and social security numbers for 145 million Americans – nearly half of the nation. The upshot was Equifax being fined £11m for the breach, and as part of the settlement being required to spend $billions in customer compensation and security upgrades.
A cyberattack causes you to breach GDPR. T-Mobile fell foul of GDPR regulations in 2021 when a cyberattack resulted in the personal data of 77 million customers being listed for sale on a cybercriminal forum. The telecoms company was ordered to pay upwards of $500 million dollars over the following two years in customer reparations, legal fees, and upgraded data security technology.
It shows that one wrong click of a button, one overlooked patch update, one unreviewed user permission, and your company could be in serious trouble – financially, reputationally, operationally… or all three.
It’s OK – our IT team has got us covered, right?
Businesses expect their IT teams to fend off these invisible threats, putting an impenetrable guard around them, 24/7.
- One in two organisations can’t track data leaving the business.
- 43.5% can’t manage cloud application usage.
- And over three-quarters can’t continuously audit cloud objects.
39% of organisations suffered data loss due to a cyberattack in 2024 – that’s up from 30% in 2021. And the human factor plays a part too: 30% lost data due to user error, and 27% due to disgruntled employees.
The threats are mounting on all sides for IT security professionals, but their team sizes are being decreased, they’re losing sleep due to worry over the risk, and even their annual leave is being interrupted to respond to threats.
‘What about AI?’ you say. ‘Surely its automation capabilities should mean our IT staff can take off as much time as they want, and our cybersecurity should remain on rails?’ Well, yes… and no. AI gives attackers just as many weapons as it gives security professionals shields.
So, what’s the answer?
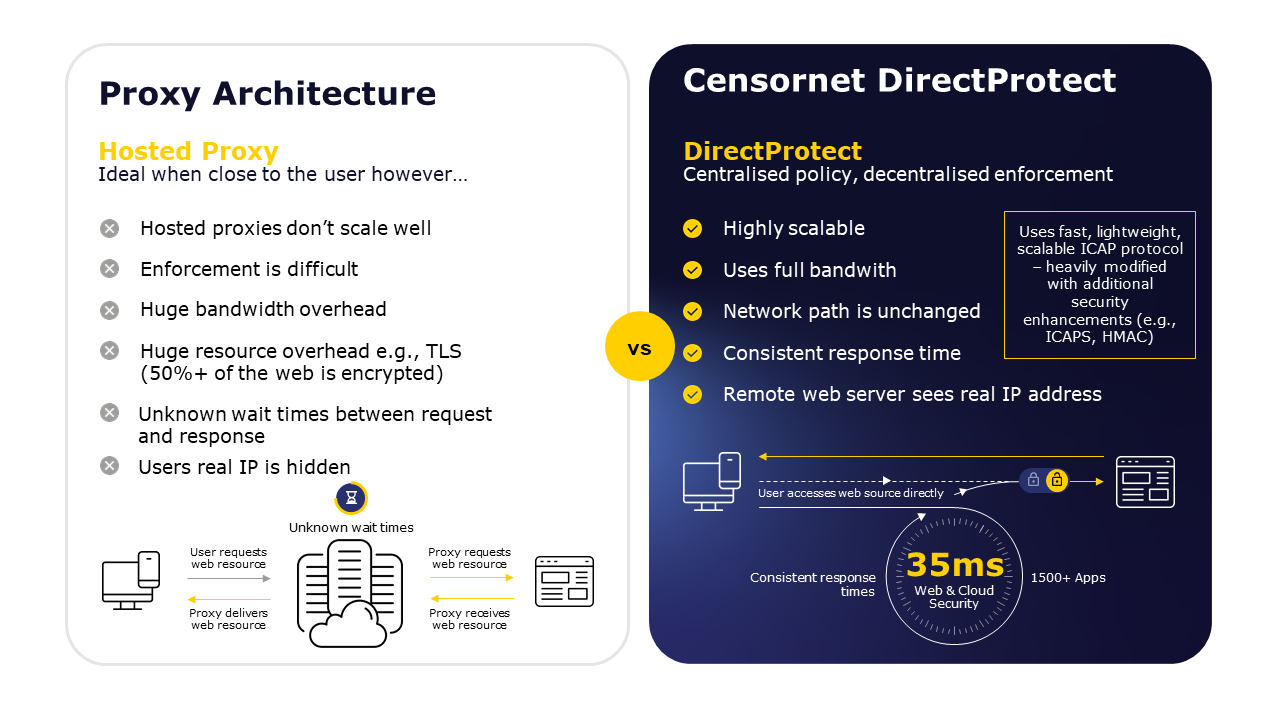
What’s needed is a security system that knows the apps and websites your company uses, it knows all the actions that your staff could take within those apps and websites, and it knows where your lines are drawn in terms of acceptable usage. It would also be ideal if such a system could be rolled out instantly, without the extensive setup that impacts hosted proxy systems. And it would be perfect if the system didn’t rely on remote data centres that are susceptible to outages and return irrelevant web results based on their geographical location.
Sounds too good to be true?
Well, Censornet’s Direct Protect architecture has enabled exactly those benefits for clients since 2015. It already protects millions of users, and processes thousands of app requests and hundreds of thousands of web actions every week.
It locks out web-borne malware and offensive or inappropriate content, manages time spent on unproductive sites, and allows access to your approved websites and cloud apps whilst controlling the activity taken upon them.
It lets organisations embrace the freedom to quickly and safely deploy new cloud apps in minutes, benefitting from the industry’s most extensive app catalogue.
And, because there’s no need for proxy web traffic, it preserves IP addresses and always maintains privacy. Controllers can instantly test policies, removing guesswork and enforcing policies direct to devices. The end result is powerful reassurance, and a fast, unobtrusive cloud and web user experience.
With architecture like Direct Protect, organisations get the scalability and flexibility of the cloud without having to sacrifice security – and without pushing already stressed IT teams into the red zone. Megan Baldwin, Information Security Manager at haysmacintyre is just one of the SMB leaders whose organisations we’ve helped to future-proof and drive towards growth without fearing a major data loss:
“It’s been a gamechanger. Now, I can definitively demonstrate what’s happening with people’s web behaviour. We’ve got control, and a chain of evidence… It means we can be more supportive. By showing that IT is part of the team, we can demonstrate how we all work together to ensure a strong security culture.”
Explore how you can scale the cloud without compromising security with our on-demand webinar, Key Concepts to Securing Cloud Applications.







