With the final few elements of the once secure citadel that was the enterprise network heading outside of the perimeter, security teams are now tasked with managing a dizzying array of remote workers, devices and applications.
The VPN has become a prominent part of this equation, securely encrypting data as it flows between the corporate data centre and employees.
However, while a VPN is an accepted way of securing data traffic, it is not without its downsides.
Specifically, it adds latency because it routes and encrypts all data through VPN termination points, which quickly become overwhelmed, translating into a miserable experience for users.
In fact, Microsoft has pointed out that the current crisis has escalated this problem significantly, stating “…. a high concurrency of users working from home generates a large volume of Microsoft 365 traffic which, if routed through forced tunnel VPN and on-premises network perimeters, causes rapid saturation and runs VPN infrastructure out of capacity.”
What is split tunnelling and how does it help reduce latency?
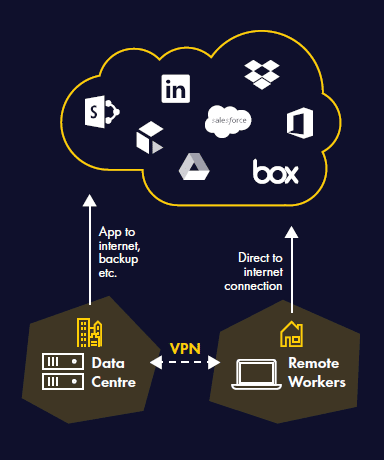
Split tunnelling is a common configuration for companies looking to overcome latency issues.
Essentially, split tunnelling involves routing only enterprise traffic that is destined for the corporate network over the VPN and encrypting connections to file servers, database servers and other technology assets.
Other traffic, such as web or cloud application traffic is sent directly to the Internet. This removes unnecessary overhead and latency – improving performance for the user.
There are two configurations of tunnel, a ‘split include tunnel’, which only protects specific traffic and a ‘split exclude tunnel’ which protects everything except a pre-designated set of traffic.
How to manage the risk from split tunnelling?
Split tunnelling offers obvious benefits, reducing friction on applications and services deemed lower risk, while protecting more sensitive data. It does, however, introduce a weak point in that a lot of the protections and countermeasures offered by the corporate environment are essentially negated.
Split tunnelling’s ability to offer direct to internet connections allows end-users to bypass proxy servers and network gateways, making it harder for traditional security solutions to monitor malicious actions and provide countermeasures.
A user on a compromised home device and network could also unwittingly provide a jumping off point for a threat actor looking to compromise a corporate system. As has been proven on a number of occasions recently, not all VPNs are secure, even now.
These problems can be addressed by using a security solution which supports direct to internet connections, as recommended by Microsoft for Microsoft 365.
With intelligent agents on endpoints, secure connections direct to web and cloud services can be provided without putting a burden on the VPN with traffic traversing corporate networks. In addition, data centre environments can be protected using a more traditional cloud gateway to protect application-to-internet traffic, when data is moved to a cloud-based backup service, for example.
Configured in this way, split tunnelling can enable users with the freedom to use cloud applications at the latency recommended by the developers of such services, whilst also protecting corporate data.
For more information on how to protect Microsoft 365 users in today’s new world of work, head over to our How to Secure Microsoft 365 hub.






