While it is generally recognised that Business Email Compromise (BEC) is a big problem for businesses, putting a number on the size of the problem is hard.
However, documents from a court case made public in Texas this week lifted the lid on some interesting details of how one attacker, Kenenty Hwan Kim, aka Myung Kim, 64, managed to take over $500,000 from just two companies.
What happened?
First, let’s state upfront that Kim managed to steal this sum of money without using any advanced technical skills. It is a perfect example of how motivated attackers don’t need to have the backing of an APT team or access to exotic Zero Days.
All he needed was access to email and the ability to manipulate people.
His first target was Solid Bridge Construction. Kim started the misdemeanour by sending phishing emails purporting to be from Brett Chance, the owner of Chance Contracting, a company which specialises in the construction of roads.
To support the scam, he had set up a bank account in the name of Chance Contracting after registering the business name in a different state. To the untrained eye, the bank accounts would look very similar.
After finding the relevant target internally, he sent emails citing ‘issues’ receiving payment checks and asked Solid Bridge to instead mail a cheque to his new bank account. Solid Bridge duly obliged, to the tune of $210,000. Once deposited, he managed to sneak $100,000 out to other accounts before being frozen under suspicious circumstances.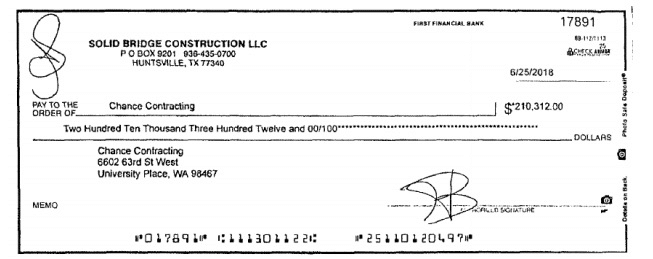
The second Business Email Compromise scam involved the much more well-known brand, Electrolux, who he managed to persuade into wiring around $333,000 to his account.
Details of exactly how he managed to achieve this are not as clear, however the court documents show he was able to convince a member of staff into thinking they were paying a vendor.
Once the money was wired, he managed to withdraw nearly a quarter of a million dollars using a cashier’s cheque and deposit it, along with $10,000 cash, into another account he ran. Some of this was subsequently transferred offshore to a co-conspirator in South Africa.
Protect against such fraud
The court case goes to show some of the scale of the impact of BEC scams, which are a combination of human and technological failings.
To address the human problem, training and awareness needs to be maintained in a way which keeps the issue on employee’s radar. An anti-phishing mind-set is hard to create, especially with BEC where the solution lies in challenging requests from senior members of staff, but such efforts are crucial.
Training should be combined with a progressive email security solution which, in itself, operates the necessary layers to address the nuances that a BEC scam include. A comprehensive solution that includes functionality to quarantine and drop emails when they are seen to be malicious, as well as offering more advanced executive monitoring capabilities such as matching real names in multiple address fields.
To ensure communications are coming from legitimate domains, it should also integrate domain and IP analysis. This will inhibit an attacker who tries to set-up domains close to, but not exactly matching, the authentic one. It should also penalise domains which have recently been registered.
Given the dominance of cloud-based email in the enterprise now with the penetration of tools such as Microsoft 365, coupled with a newly remote workforce, Multi-Factor Authentication (MFA) can also be invaluable in the fight against BEC. MFA will address the issue of any attacker looking to use stolen credentials to gain access to a user’s emails and insert themselves into the flow of conversation for malicious purposes.
As we have seen in this case, Business Email Compromise is a problem borne of people and executed by people, but it is one which requires a hybrid of technology and humans to address.
For more insight on how you can secure your organisation against BEC and more advanced threats, go to our How to Secure Microsoft 365 hub.





