In an age of APT groups, custom malware and zero-days, the security industry tends to forget that the age-old phishing attack is still one of the main routes to data breach.
Such threats are also continually advancing; if people are the soft underbelly of security strategies, then cyber criminals are incessantly sharpening the knife needed to slice them open.
A perfect example of this is the recent discovery by researchers at Cofense of a phishing attack that attempts to lure Microsoft 365 users into giving criminals access to data by abusing 0Auth2 and OpenID Connect (OIDC) protocols.
As with most phishing, the example investigated started with an emotionally charged and all too good to be true email lure. This one promised the mark information about a bonus, with a link to an Microsoft 365 drive.
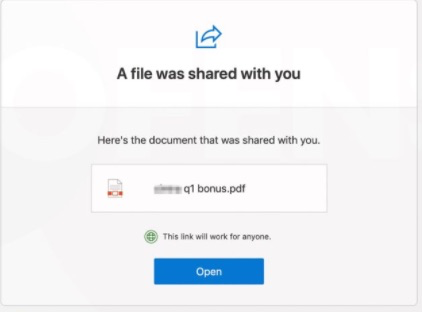
Keen to understand how much money they had been awarded, employees would click on a link to a legitimate Microsoft 365 login page at login.microsoftonline.com
This, however, was where the legitimacy stopped. Closer inspection of the URL showed redirections to a server in Bulgaria which would trick individual users into giving permissions to a malicious application, seemingly as part of the normal flow of interactions, using 0Auth2 and OIDC.
Not only does this completely negate multi-factor authentication (MFA), it also grants the threat actor seemingly user approved access to their endpoint and associated cloud environment.
Once permissions were given by the user, it gave the attacker access to a variety of sensitive data including all contacts and files accessible to them, both their own and shared.
Interestingly, the attacker also had the ability to issue and refresh their own tokens for an indefinite period of time meaning they could remain hidden on an endpoint for as long as they like, siphoning off data.
What does this phishing approach mean for organisations?
From a strategy point of view, it’s evidence of the need to stay alert to the dangers of evolving phishing attacks. Security teams could be accused of complacency with email borne attacks, assuming iterative advances in this specific part of the threat landscape are largely variations on existing themes which are therefore matched by electronic countermeasures.
However, this attack underlines the ability of threat actors to launch left-field phishing approaches which go undetected by automated solutions, as they operate outside pre-defined parameters.
The other thing to take into account on this attack is that it completely sidesteps MFA, bypassing a protection that many use as a fallback layer against the problem of vulnerable users. User authenticated tokens have a level of assumed authority at a deeper level than that presided over by MFA. This should serve as a wakeup call that authentication is no panacea.
What should organisations do to protect from cyber criminals abusing 0Auth2?
A good defence against such an attack is, as in many cases, layered. Firstly, for this specific attack, people need to ensure the malicious domain masquerading as Microsoft 365, hosted at officehnoc[.]com/office – 88[.]80[.]148[.]31, is included in block lists.
Secondly, as a precaution against similar types of attacks, ensure any web filtering employed on phishing works not just on initial domains, but redirects as well. Censornet’s LinkScan technology, for example, follows redirects to their conclusion to ensure that the destination domain is not hosting malicious content. This would have caught the ‘hop’ taking the user to the Bulgarian server after the initial seemingly legitimate domain.
Ensuring your anti-phishing approach is based on multiple threat intelligence feeds will also put your organisation on the front foot when it comes to protecting against the never-ending cycle of such attacks. However, this needs to be done in an easy to manage way to prevent threat data overload, as with our consolidated cloud security platform.
In a fast paced and often confusing threat landscape, education is a big part of addressing the phishing puzzle. For free informative resources on how to keep Microsoft Microsoft 365 users safe, visit our Defence365 hub.