Email, when it was initially adopted, was inherently insecure – by default email traffic is unencrypted – and most people regarded email communication as the electronic equivalent to an informal chat by the coffee machine.
As it became a business-critical tool, threat actors saw an opportunity to make money. Typically, this manifested itself as large-scale spam runs hoping to trick susceptible employees into clicking on bad links or opening malicious attachments. It was a numbers game. The industry responded with recurrent pattern matching to identify mass unsolicited mailings.
Now, with nearly 3.7bn email accounts currently in use, the opportunity email presents as an attack vector for criminals hasn’t changed. Large scale spam runs have morphed into more targeted phishing attacks and malware is still delivered via email – although with more complex delivery mechanisms.
Ever creative, attackers have realised the limitations of traditional countermeasures and adapted, nuancing the markers of attack to hide amidst the mass of traffic that a modern enterprise now sends and receives. Operating at the edges, email threats are now researched and crafted using simple plain text messages sent from well-configured domains to stay off the radar.
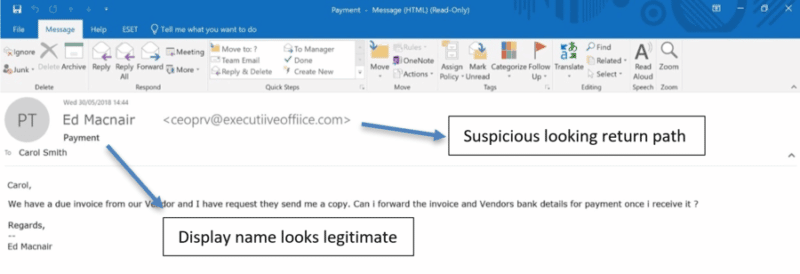
Let’s look at the example below. A relatively simple attack to carry out, all the attacker has had to do in this situation is research the names of the recipient and the supposed sender, change the display name in the Header From field and it looks like a relatively convincing email. The only true marker of malicious activity is the Envelope From / Return Path, which is clearly suspicious.
In this case, if nothing about the sender or sending server was suspicious, if the domain wasn’t recently registered and if the SPF record was valid, this email may have made it through front-line email security. In addition, the language used is also general enough to walk through lexical analysis checks.
Another example of how email attacks have evolved to hide amongst the morass of unstructured enterprise data is by using cloud channels to deliver payloads. This moves threats away from areas deemed as the traditional attack surface for email security.
For example, malware authors no longer hard code C&C IP addresses into their droppers when calling home. Instead, they place the payload on a rotating set of Dropbox, Box or other cloud file storage servers, meaning the call home now no longer has a single point of failure. What’s more, the malicious call is to a legitimate well-known trusted cloud app domain.
For example, malware authors no longer hard code C&C IP addresses into their droppers when calling home. Instead, they place the payload on a rotating set of Dropbox, Box or other cloud file storage servers, meaning the call home now no longer has a single point of failure. What’s more, the malicious call is to a legitimate well-known trusted cloud app domain.
What does this all mean for your business?
This means two things for defenders. First and foremost, for the increasing amount of companies moving to cloud-based ways of working such as Microsoft 365 (formerly Office 365), there is a need for a specialist email security solution.
Microsoft’s EOP and ATP solutions offer a basic layer of protection, but it may not be intelligent enough to provide enterprise-grade protection against the threats mentioned. The economics do not stack up to allow a company the size of Microsoft to focus in detail on the nuances of a rapidly advancing email attack landscape.
For example, Microsoft’s protection against modern targeted email threats, and zero-day malware, requires ATP and there is definite well-documented room for improvement.
Secondly, companies need to embrace the idea of layered email protection. As with most email security solutions – a mesh of complementary technologies enables companies to deal with more advanced attacks.
For email, this means making sure you have countermeasures which cover the full stack; AV analysis and machine checks on factors such as sender and sending server at the basic end of the spectrum, through to advanced features such executive monitoring and algorithmic analysis.
It is also increasingly important to incorporate threat intel which can identify domain registrants with a dubious background, as attackers have become more adept at configuring attack infrastructure.
In addition, a layered solution which has visibility of the full attack chain is also important. Given many attacks are now multi-channel, it is crucial to understand how threats are moving from email across the variety of cloud apps now used by most enterprises.
For more information on how best to configure your defensive email posture, particularly when using Microsoft 365, visit our dedicated Defence365 hub.
Defence265 Vlog: How to protect your organisation from advanced email threats





