Cyber criminals often focus their attacks on email as a direct line to exploit employees. It’s easy to see why, email is such an established and popular attack vector when you consider that, by 2017, the number of email users was around 3.7 billion – approximately half of the worldwide population. Despite the adoption of other communication platforms, email is expected to grow 4.4% annually through 2021, taking the total number of email users to over 4.1 billion globally.
In recent years, the email security threat landscape has transformed. With more and more businesses migrating to Microsoft 365, it’s important that they implement the necessary layers of security to fend off modern attacks.
Over a series of blogs, we are going to take an in-depth look at how to protect from the latest and most advanced email security threats. We begin in this blog with an overview of what’s hot and what’s not in the modern email threat landscape.
NOT – Goodbye Spam!
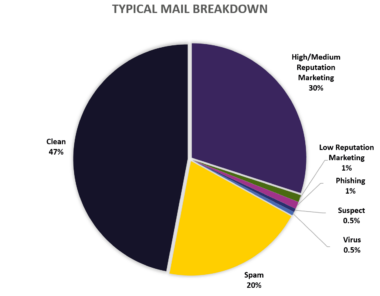 A story as old as time, unsolicited emails sent out in bulk to generate per click revenue. In the past, spam was the bane of an organisation’s messaging team because of the volume of unwanted email traffic and the impact to systems (mail servers) and users.
A story as old as time, unsolicited emails sent out in bulk to generate per click revenue. In the past, spam was the bane of an organisation’s messaging team because of the volume of unwanted email traffic and the impact to systems (mail servers) and users.
Spam still makes up a significant percentage of typical mail flow but email filtering has improved dramatically in response. Nowadays, employees are rarely exposed to the old-fashioned, large scale generic spam email because it goes straight to their junk folder or to quarantine.
NOT – ‘Wide net’ phishing attacks
Another tried and tested technique, phishing attacks involves sending fraudulent emails that claim to be from reputable companies to mislead individuals into revealing sensitive information. Like spam emails, it is on the radar of every security team, but it can still cause havoc if an attack slips through.
Over time, the crude mass-email with a compromised link or attachment has fallen out of vogue and cyber attackers have moved towards more sophisticated and targeted emails to catch employees out. Whilst phishing tactics have evolved, so has email link protection to meet the challenge.
Our LinkScan™ technology protects users from links in messages at time-of-click and works effectively against the latest multi-channel attacks that start over email but quickly move to the web or cloud channels. It also follows redirects and scans for malicious links in the final target if the final target is a file object.
HOT – Impersonation attacks
As more nuanced phishing threats continue to be the scourge of security teams, nothing encapsulates the targeted and sophisticated tactics of modern cyber criminals quite like Business Email Compromise (BEC), also known as CEO fraud.
A 2019 Europol report found that BEC continues to feature on the top ten concerns for EU organisations. The term BEC refers to fraudsters posing as a CEO or a senior employee and asking the victim over email to transfer a significant sum of money or carry out other fraudulent activity.
BEC has increased steadily and now accounts for 1 percent of all emails. Lloyds Bank has calculated the average loss to SMEs as a result of BEC is £27,000 and identified that 6 percent of SMEs had to make employees redundant due to the financial impact of falling for the ploy, which demonstrates the significant impact the technique is having on organisations.
The importance of training employees to recognise these more sophisticated techniques cannot be understated. However, BEC scams rely on ‘social engineering’ to take advantage of a human desire to please a high-ranking executive. For this reason, businesses require ultra-modern technology such as algorithmic analysis, threat intelligence and executive name checking to provide multi-layered email security protection.
For these tools, which protect against the most sophisticated types of attack, organisations have to look beyond the security that’s provided in M365, to security providers who can layer on additional protection.
HOT – Account Takeover Attacks
A relatively new technique, Account Takeover (ATO) is a form of identity theft where a fraudster gains access to a victim’s email account. ATO attacks are often targeted at a specific organisation and combined with social engineering or phishing initially, to trick employees into sharing their Microsoft 365 (M365) credentials.
Credential Stuffing, using lists of email addresses and passwords from multiple large scale breaches, is also common. This could mean that a hacker not only gains access to a business’ emails but the entire suite of products.
The potential impact of Account Takeover is enormous, leading to sustained and varied impersonation campaigns. Attackers are well funded, sophisticated and organised so their approach is highly targeted and well researched. M365 is an active target for these cyber criminals, with more than 300 million fraudulent sign-in attempts to their cloud services every day.
When it comes to Account Takeover, multi-factor authentication (MFA) is key. MFA protects user accounts with more than just a password. Even if an attacker cracks, steals or otherwise obtains a user’s M365 credentials, MFA can protect access to their sensitive data with an added layer of security.
Hedge your bets on email security threats
When it comes to keeping emails secure, employee awareness needs to be combined with a multi-layered approach to email security that utilises the appropriate technologies. Although M365 offers protection against established threats such as spam, traditional pattern matching technologies are almost entirely useless against modern email attacks.
Organisations need to add a layer of email security that combines algorithmic analysis, threat intelligence and executive name checking to efficiently protect themselves. The addition of MFA can also increase confidence further, providing an extra layer of protection.
To help keep organisations safe while using Microsoft 365 for email – and more – we have created Defence365, a practical best-of-breed email security solution provided alongside expert advice, to enhance the protection and performance of your M365 environment. To find out more about how we can help you secure email in your business visit our Defence365 hub or arrange a conversation with one of our experts.
Defence365 Vlog: How to protect your organisation from advanced email threats





